Highlights (Core)
| Panel | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ||||||||||||
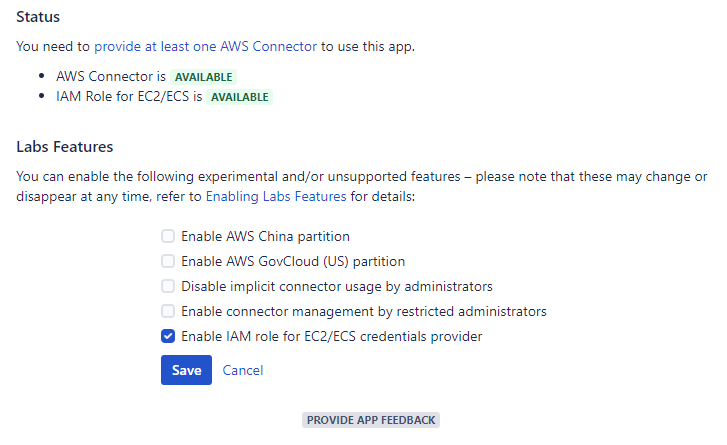
Provide AWS security credentials via an IAM role for EC2/ECSYou can now enable the IAM role for EC2/ECS credentials provider via a feature flag. If you have provisioned your Atlassian workloads on Amazon EC2 (for example, via the Atlassian Data Center on AWS Quick Starts), Amazon ECS, or AWS Fargate, you can now benefit from the convenience and flexibility of providing AWS security credentials via IAM roles for Amazon EC2 instances and IAM roles for Amazon ECS tasks.
|
Highlights (Bamboo)
| Panel | ||||
|---|---|---|---|---|
| ||||
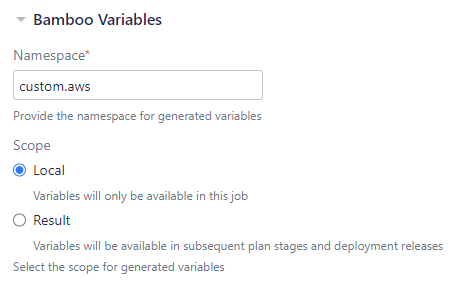
Adjust generated Bamboo variable namespace and scopeSimilar to the Inject Bamboo variables task that has been included with Bamboo as of release 6.7, you can now specify the namespace and scope for Bamboo variables generated by the AWS Credentials Variables and Amazon ECR Credentials Variables tasks to enable more flexible build orchestration. You can now pass a variable between stages, pass a variable from a plan to a deployment project, and you can use multiple tasks within the same job without overriding variables from preceding tasks by adjusting the namespace. The tasks default to the preceding behavior with |
Resolved issues
Release 2.14.0
2020-10-20
This release addresses the following issues:
Core
Stories
IFAWS-301 (UAA-49) – As an administrator, I want to provide AWS credentials via an IAM role for EC2 so that I do not need to add an access key
Improvements
IFAWS-1339 – Add app configuration link tooltip
Bugs
IFAWS-1359 – Fix missing 40x when using PUT with additional JSON fields
IFAWS-1376 (UAA-435) – Fix GET not returning the JSON field when connector scope has not been configured
IFAWS-1438 (UAA-462) – Fix insufficient credentials validation of access key dialog
Bamboo
Stories
IFAWS-1423 – As a user, I want to be in control of variable namespace and scope so that I gain simplified plan composition
Tasks
IFAWS-1350 – Drop support for Bamboo 6.5
IFAWS-1403 – Drop support for Bamboo 6.6
Bitbucket
Tasks
IFAWS-1348 – Drop support for Bitbucket 5.9
IFAWS-1351 – Drop support for Bitbucket 5.10
IFAWS-1353 – Drop support for Bitbucket 5.11
IFAWS-1405 – Drop support for Bitbucket 5.12
IFAWS-1407 – Drop support for Bitbucket 5.13
IFAWS-1410 – Drop support for Bitbucket 5.14
Confluence
Tasks
IFAWS-1347 – Drop support for Confluence 6.8
IFAWS-1352 – Drop support for Confluence 6.9
IFAWS-1404 – Drop support for Confluence 6.10
IFAWS-1408 – Drop support for Confluence 6.11
Jira
Tasks
IFAWS-1349 – Drop support for Jira 7.9
IFAWS-1354 – Drop support for Jira 710
IFAWS-1406 – Drop support for Jira 7.11
IFAWS-1409 – Drop support for Jira 7.12