Highlights (Core)
Evaluate remote conditions with the Get Systems Manager Parameter actionYou can now use the Get Systems Manager Parameter action in applicable integrations to evaluate arbitrary remote conditions by persisting a JSON result shape that adheres to the action response format schema:
This allows you to use an event-based architecture to decouple condition evaluation in AWS from condition evaluation in Atlassian to ensure that any prerequisites for your workflows are automatically checked right before dependent steps are initiated, thereby reducing cost and latency over using the Invoke Lambda Function action to synchronously call AWS services and third-party REST APIs at evaluation time. Currently supported integrations are the Jira Service Management Automate with AWS if condition, the Jira Automate with AWS workflow condition and Automate with AWS workflow validator, and the Bamboo Automate with AWS task. |
Inject remote configuration data and secrets with the Get Systems Manager Parameter actionYou can now use the Get Systems Manager Parameter action in applicable integrations to inject arbitrary remote configuration data and secrets via the Systems Manager Parameter Store: This allows you to maintain configuration data and regular secrets as (secure) parameters in the Systems Manager Parameter Store, and optionally maintain secrets in AWS Secrets Manager when you require more advanced secret lifecycle management.
Currently supported integrations are the Bamboo Automate with AWS task. |
Provide AWS security credentials via an IAM role for EC2/ECS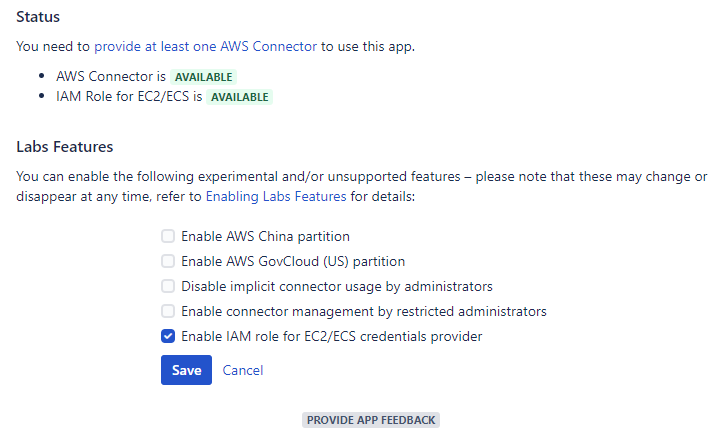 You can now enable the IAM role for EC2/ECS credentials provider via a feature flag. If you have provisioned your Atlassian product on Amazon EC2 (for example, via the Atlassian Data Center on AWS Quick Starts), Amazon ECS, or AWS Fargate, you can now benefit from the convenience and flexibility of providing AWS security credentials via IAM roles for Amazon EC2 instances and IAM roles for Amazon ECS tasks.
|
Highlights (Bamboo)
Adjust generated Bamboo variable namespace and scope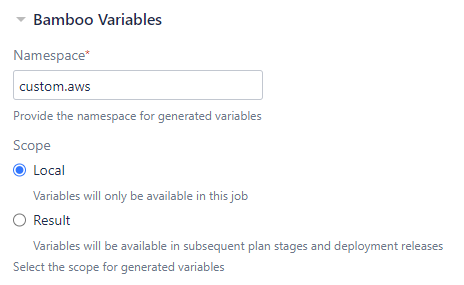 Similar to the Inject Bamboo variables task that has been included with Bamboo as of release 6.7, you can now specify the namespace and scope for Bamboo variables generated by the Automate with AWS task to enable more flexible build orchestration. You can now pass a variable between stages, pass a variable from a plan to a deployment project, and you can use multiple tasks within the same job without overriding variables from preceding tasks by adjusting the namespace. The task defaults to the preceding behavior with |
Resolved issues
Release 1.9.2
2021-05-18
This release addresses the following issues:
Core
Improvements
AAWS-876 – Update Identity Federation for AWS dependency to 2.14.2
Bamboo
Bugs
AAWS-877 – Fix erroneous script tag usage in Bamboo tasks
Release 1.9.1
2021-05-18
This release addresses the following issues:
Core
Improvements
AAWS-845 – Surface new AWS region Asia Pacific (Osaka) / ap-northeast-3
AAWS-850 – Update Identity Federation for AWS dependency to 2.14.1
Release 1.9.0
2020-11-30
This release addresses the following issues:
Core
Stories
AAWS-731 – As a user, I want to get a Systems Manager (SSM) parameter so that I can inject remote data
AAWS-739 – As a user, I want to get a Systems Manager (SSM) parameter so that I can check remote conditions
Jira
Tasks
AAWS-759 – Drop support for Jira 7.9
AAWS-764 – Drop support for Jira 7.10
AAWS-802 – Drop support for Jira 7.11
AAWS-805 – Drop support for Jira 7.12
Bamboo
Stories
AAWS-814 – As a user, I want to be in control of variable namespace and scope so that I gain simplified plan composition
Tasks
AAWS-760 – Drop support for Bamboo 6.5
AAWS-799 – Drop support for Bamboo 6.6
