| Include Page | ||||
|---|---|---|---|---|
|
Configuration
| Tip |
|---|
Use Amazon ECR Credentials with Bamboo Docker task The most frequent use case for the Amazon ECR Credentials Variables task is to enable the built-in Bamboo Docker task to push images to an Amazon ECR repository - refer to How to push a Docker image to a repository in your Amazon ECR registry with the Bamboo Docker task for details. |
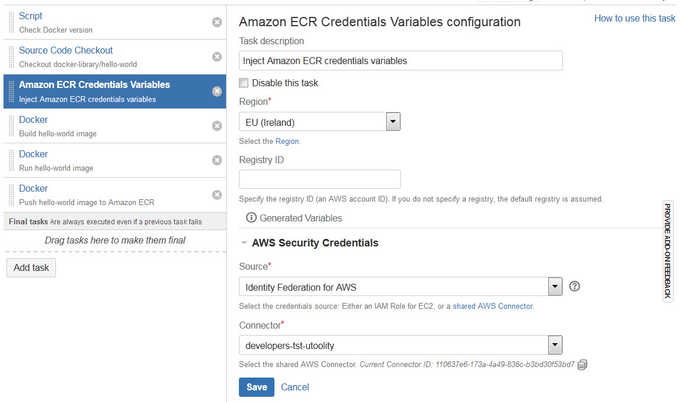
To configure an Amazon ECR Credentials Variables task:
Navigate to the Tasks configuration tab for the job (this will be the default job if creating a new plan).
Click the name of an existing Amazon ECR Credentials Variables task, or click Add Task and then Amazon ECR Credentials Variables to create a new task.
Complete the following settings:
Task Description | (Optional) Identify the purpose of the task. |
Disable this task | Check, or clear, to selectively run this task. |
Region | Select the desired AWS Region. Alternatively, select [Use region variable ...] to supply the region dynamically via Bamboo variables (needs to be a region code such as |
Registry ID | (Optional) Select the AWS account ID that is associated with the registry for which to get authorization credentials
|
Bamboo Variables | |
Namespace | Provide the namespace for generated variables |
Scope | Select the scope for generated variables:
|
AWS Security Credentials | |
Source | Select the AWS Credentials Source (see below). Can be either Identity Federation for AWS or an IAM Role for EC2. |
Connector | (Conditional) Select the shared Identity Federation for AWS Connector. Alternatively, select [Use connector variable ...] to supply the connector dynamically via Bamboo variables (needs to be a connector id such as |
Role ARN | (Conditional | Optional) Specify the ARN of another role that the agent's IAM role for EC2 should assume. |
AWS Credentials Sources
![]() Managed IAM Policy
Managed IAM Policy
We recommend to facilitate an available AWS Managed Policy to ease permission maintenance - the Amazon ECR Credentials Variables task requires the permissions in the AmazonEC2ContainerRegistryPowerUser managed policy, which at the time of this writing looks as follows:
| Code Block |
|---|
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Action": [
"ecr:GetAuthorizationToken",
"ecr:BatchCheckLayerAvailability",
"ecr:GetDownloadUrlForLayer",
"ecr:GetRepositoryPolicy",
"ecr:DescribeRepositories",
"ecr:ListImages",
"ecr:BatchGetImage",
"ecr:InitiateLayerUpload",
"ecr:UploadLayerPart",
"ecr:CompleteLayerUpload",
"ecr:PutImage"
],
"Resource": "*"
}]
} |
You have the following options to provide AWS Security Credentials:
| Include Page | ||||
|---|---|---|---|---|
|
| Include Page | ||||
|---|---|---|---|---|
|
Usage
Bamboo variables
This task generates the following Bamboo variables for reuse in subsequent tasks without native integration with Identity Federation for AWS:
Bamboo variables
| Code Block | ||
|---|---|---|
| ||
${bamboo.custom.aws.ecr.authorizationToken.password}
${bamboo.custom.aws.ecr.expirationDate}
${bamboo.custom.aws.ecr.proxyEndpoint}
${bamboo.custom.aws.ecr.proxyEndpointDomain}
${bamboo.custom.aws.ecr.username}
${bamboo.custom.aws.ecr.password} |
| Info |
|---|
The '*.password' suffix ensures that sensitive variables are masked with asterisks ('*******') in the Bamboo build log. |
An alternative representation as a JSON object for automated processing with tools like jq is available too:
Bamboo variables (alternative representations)
| Code Block | ||
|---|---|---|
| ||
${bamboo.custom.aws.ecr.credentials.json.password} |
Environment variables
Aforementioned variables will also be available as environment variables for use in Bamboo Script tasks. The syntax differs between shells, as illustrated in these examples for assigning them to the standardized variables used by tools like the AWS Command Line Interface (AWS CLI):
Bash (Unix shell)
| Code Block | ||
|---|---|---|
| ||
export AUTHORIZATION_TOKEN=$bamboo_custom_aws_ecr_authorizationToken_password export EXPIRATION_DATE=$bamboo_custom_aws_ecr_expirationDate export PROXY_ENDPOINT=$bamboo_custom_aws_ecr_proxyEndpoint export PROXY_ENDPOINT_DOMAIN=$bamboo_custom_aws_ecr_proxyEndpointDomain export USERNAME=$bamboo_custom_aws_ecr_username export PASSWORD=$bamboo_custom_aws_ecr_password |
PowerShell
| Code Block | ||
|---|---|---|
| ||
$AUTHORIZATION_TOKEN = $Env:bamboo_custom_aws_ecr_authorizationToken_password $EXPIRATION_DATE = $Env:bamboo_custom_aws_ecr_expirationDate $PROXY_ENDPOINT = $Env:bamboo_custom_aws_ecr_proxyEndpoint $PROXY_ENDPOINT_DOMAIN = $Env:bamboo_custom_aws_ecr_proxyEndpointDomain $USERNAME = $Env:bamboo_custom_aws_ecr_username $PASSWORD = $Env:bamboo_custom_aws_ecr_password |
Windows Command Prompt (cmd)
| Code Block | ||
|---|---|---|
| ||
set AUTHORIZATION_TOKEN=%bamboo_custom_aws_ecr_authorizationToken_password% set EXPIRATION_DATE=%bamboo_custom_aws_ecr_expirationDate% set PROXY_ENDPOINT=%bamboo_custom_aws_ecr_proxyEndpoint% set PROXY_ENDPOINT_DOMAIN=%bamboo_custom_aws_ecr_proxyEndpointDomain% set USERNAME=%bamboo_custom_aws_ecr_username% set PASSWORD=%bamboo_custom_aws_ecr_password% |
How-to Articles
| Filter by label (Content by label) | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
|
Frequently Asked Questions (FAQ)
| Include Page | ||||
|---|---|---|---|---|
|
| Questionslist macro | ||||||||
|---|---|---|---|---|---|---|---|---|
|